Kubernetes Security: Open Policy Agent Support in Prisma Cloud
You don’t have to look far to see that Kubernetes continues to grow as a leading technology in the cloud native ecosystem. In the State of Cloud Native Security 2020 survey, managed container services such as Kubernetes accounted for 21% of all workloads on average. With this adoption comes many associated projects and technologies, particularly around deployment security and compliance. That's why Prisma Cloud offers Open Policy Agent support.
What Is Open Policy Agent?
Open Policy Agent (OPA) is an open-source, general-purpose policy engine that unifies policy enforcement across the cloud native stack. OPA provides a high-level declarative language, called Rego, which lets users specify policy as code with simple APIs to offload policy decision-making from user software. OPA can help enforce policies in microservices, Kubernetes, CI/CD pipelines, API gateways and more.
OPA adoption seems to be on the upswing. In the Cloud Native Computing Foundation’s latest survey, over 75% of respondents said they were using Kubernetes, a 20% increase from the previous year’s survey.
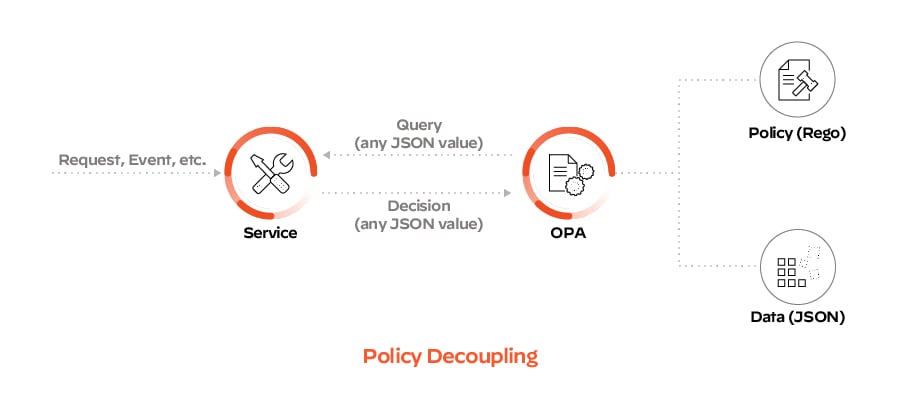
How Prisma Cloud Supports Open Policy Agent
Prisma Cloud leverages the Rego language users are already familiar with to create OPA policies directly in the Prisma Cloud UI, and implements those policies with an admission controller. Policies can be created and managed within the access control policy engine and then stored in both the console and defender.
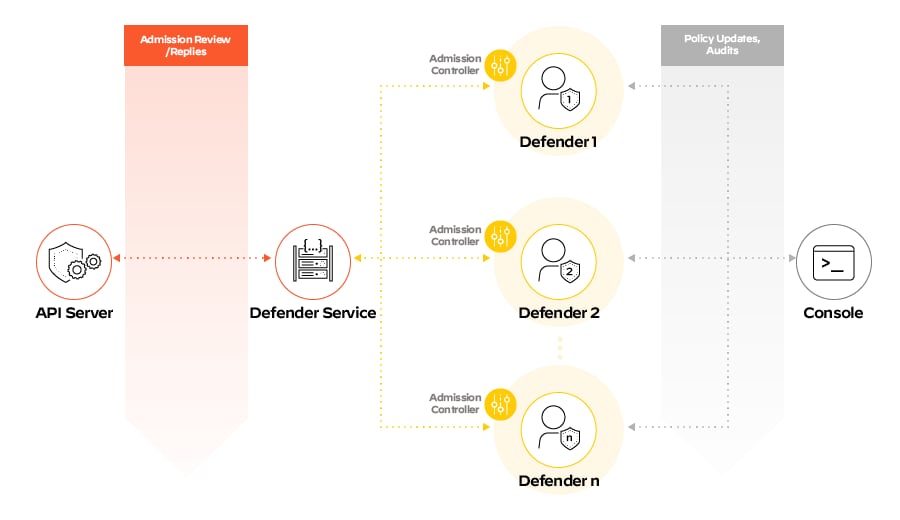
Creating an Example OPA Rule and Viewing Audits
Within Prisma Cloud users will find default rules that have been pre-created by our team, but also have the ability to create additional rules using code snippets within the UI.
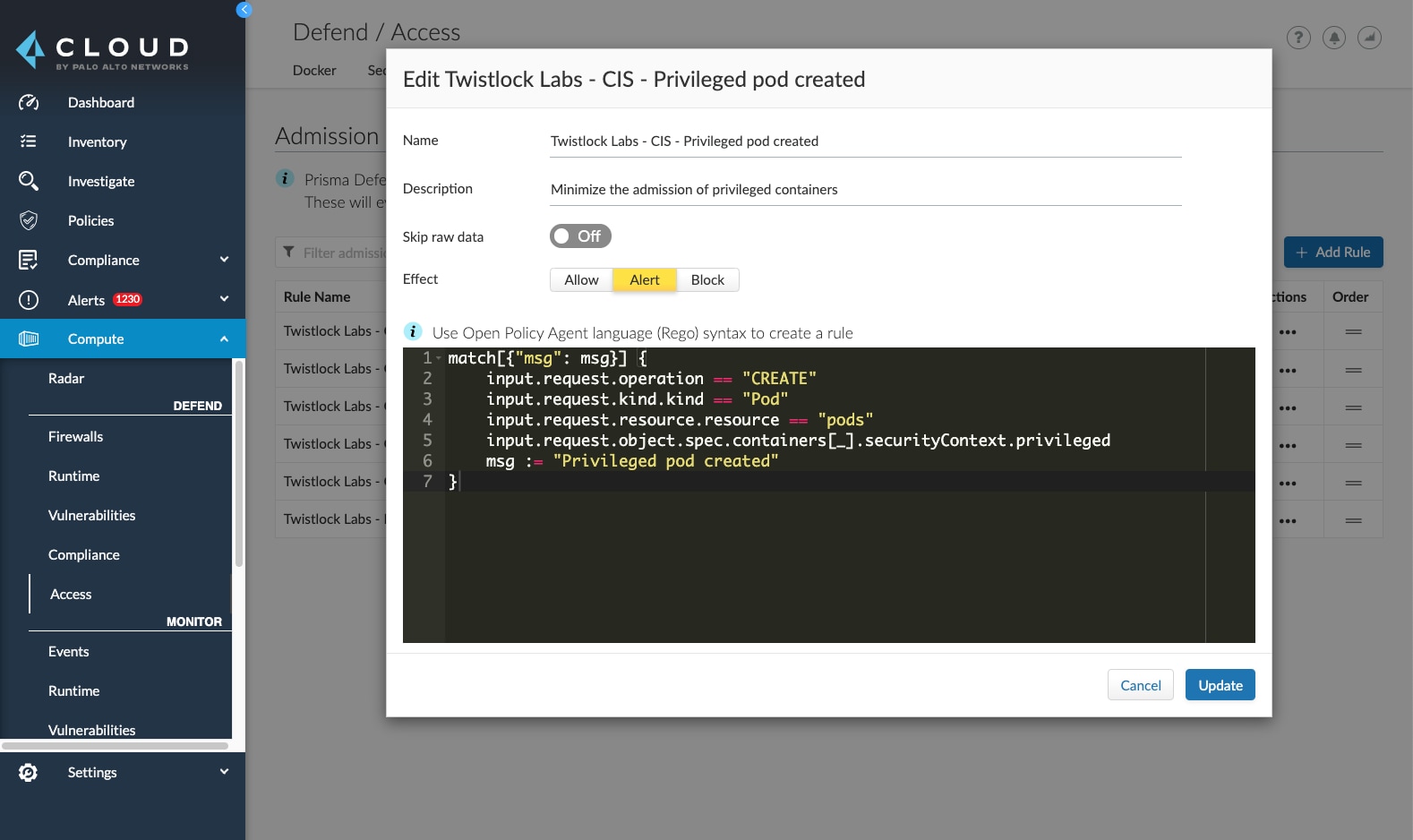
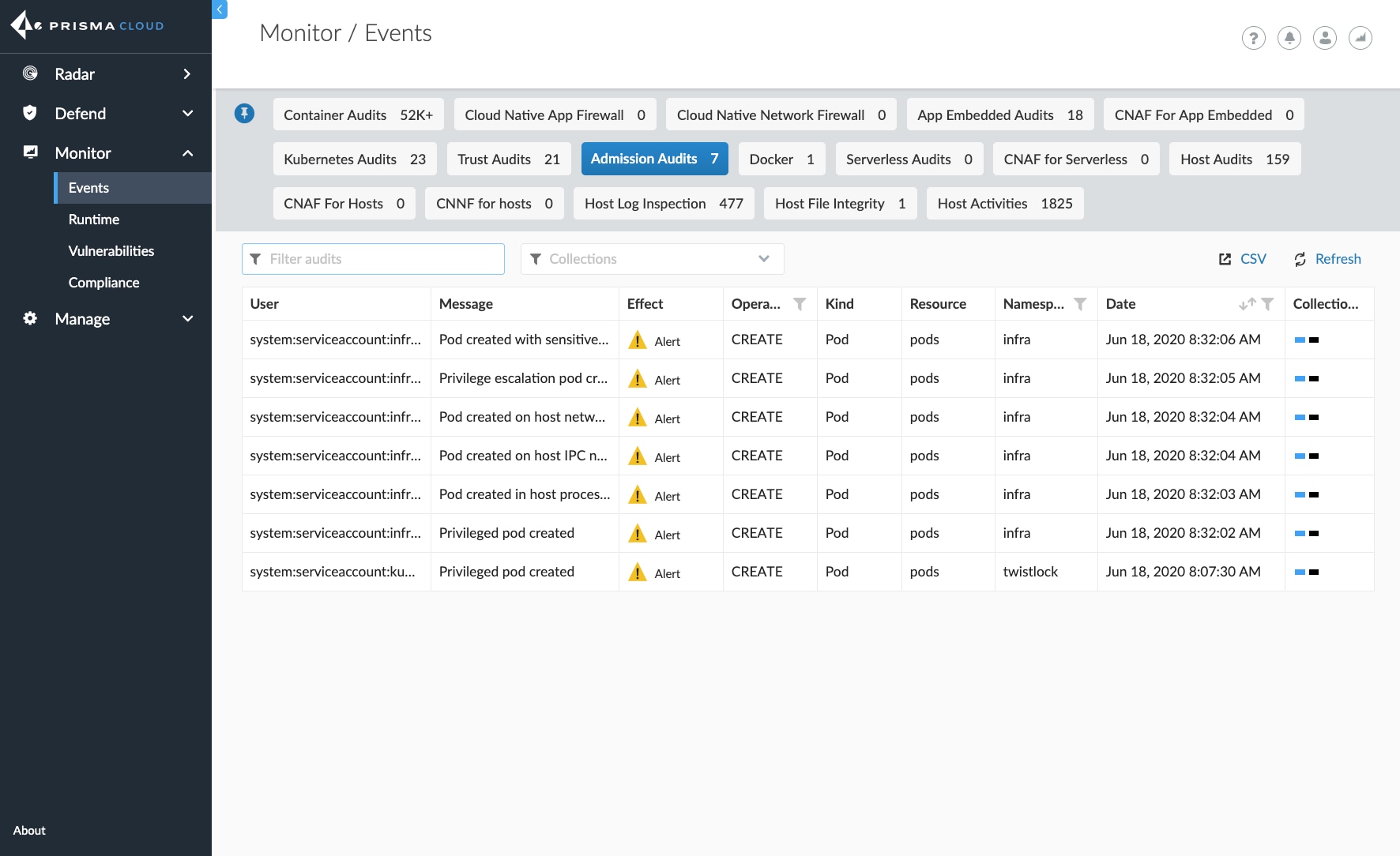
In my demo rule above, Prisma Cloud will alert on any privileged pods that are created in my environment. Then, any alerts or prevented activity will be shown in the events tab under admission audits, as shown below.
Start Using OPA Rules in Prisma Cloud
As developers and DevOps teams continue to deploy more quickly, security teams will want to ensure that any Kubernetes deployment meets specific vulnerability requirements and compliance levels. This Open Policy Agent support provides another way to achieve secure deployments with Prisma Cloud.
To learn more about how DevOps and DevSecOps are managing cloud deployments, check out the State of Cloud Native Security 2020, a recent global survey of DevOps and security leaders.
Related Blogs
Subscribe to Cloud Native Security Blogs!
By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement. Please look for a confirmation email from us. If you don't receive it in the next 10 minutes, please check your spam folder.