The Pipeline Operator
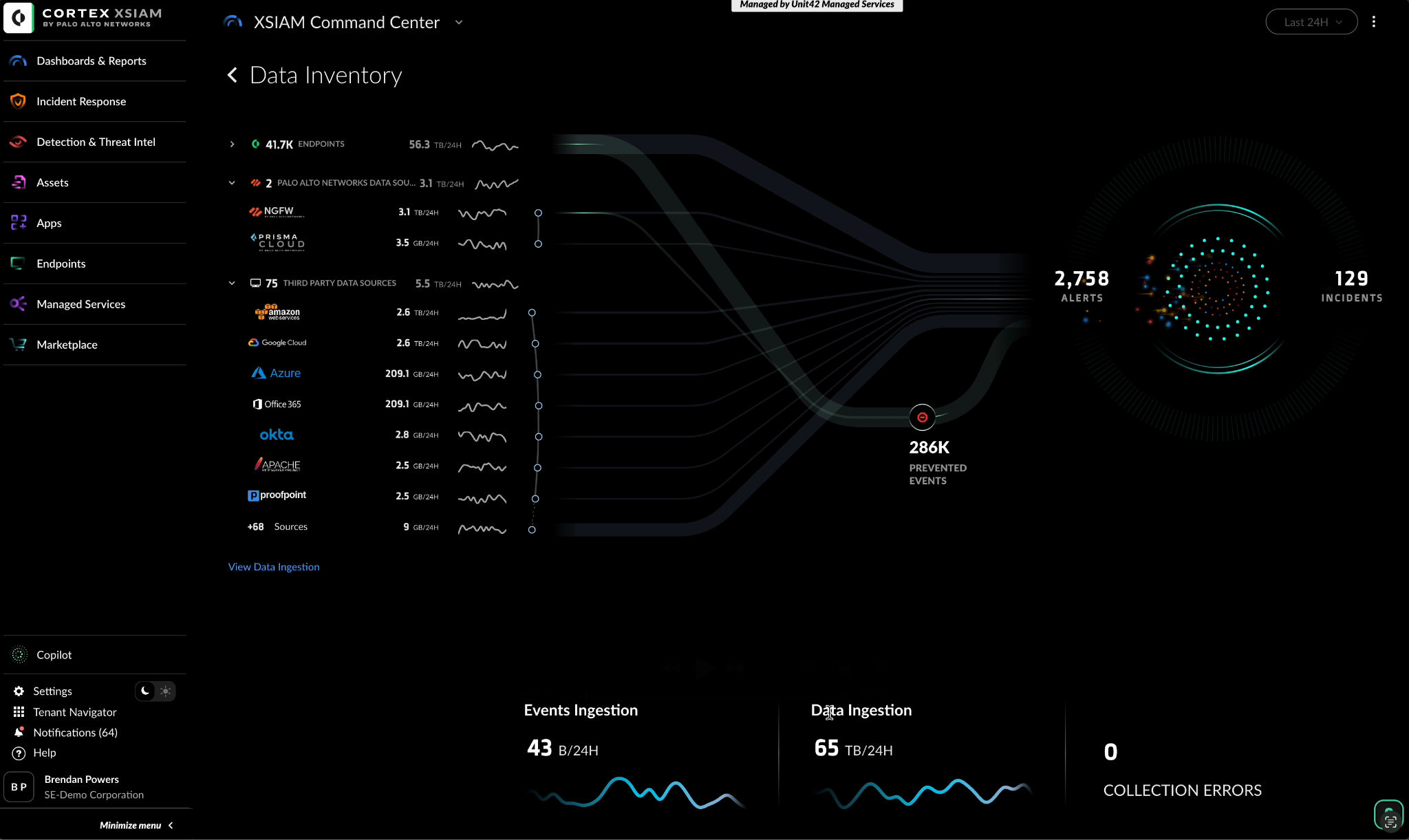
In a stretch of flat country where winter light feels thin as paper, a North American pipeline operator had grown used to living under a landslide of alerts. Two-million logs an hour, each one demanding a glance, none offering a clear story. Analysts drifted between SIEM, SOAR, and endpoint consoles, chasing ghosts until sunrise.
They began the migration in quiet increments—first a pilot, then a wider cut-over. Cortex XSIAM accepted every flow of data without argument. Thousand-line parsers became one-click connectors; out-of-the-box detectors replaced hand-written rules. Within weeks the noise resolved itself: thousands of alerts collapsed into a single, coherent incident that mapped the breach attempt from first probe to final block.
Mean time to respond fell by 98 percent. 75 percent of alerts vanished into automation. On the overnight shift the SOC finally heard something rare: silence.
The Global Exchange
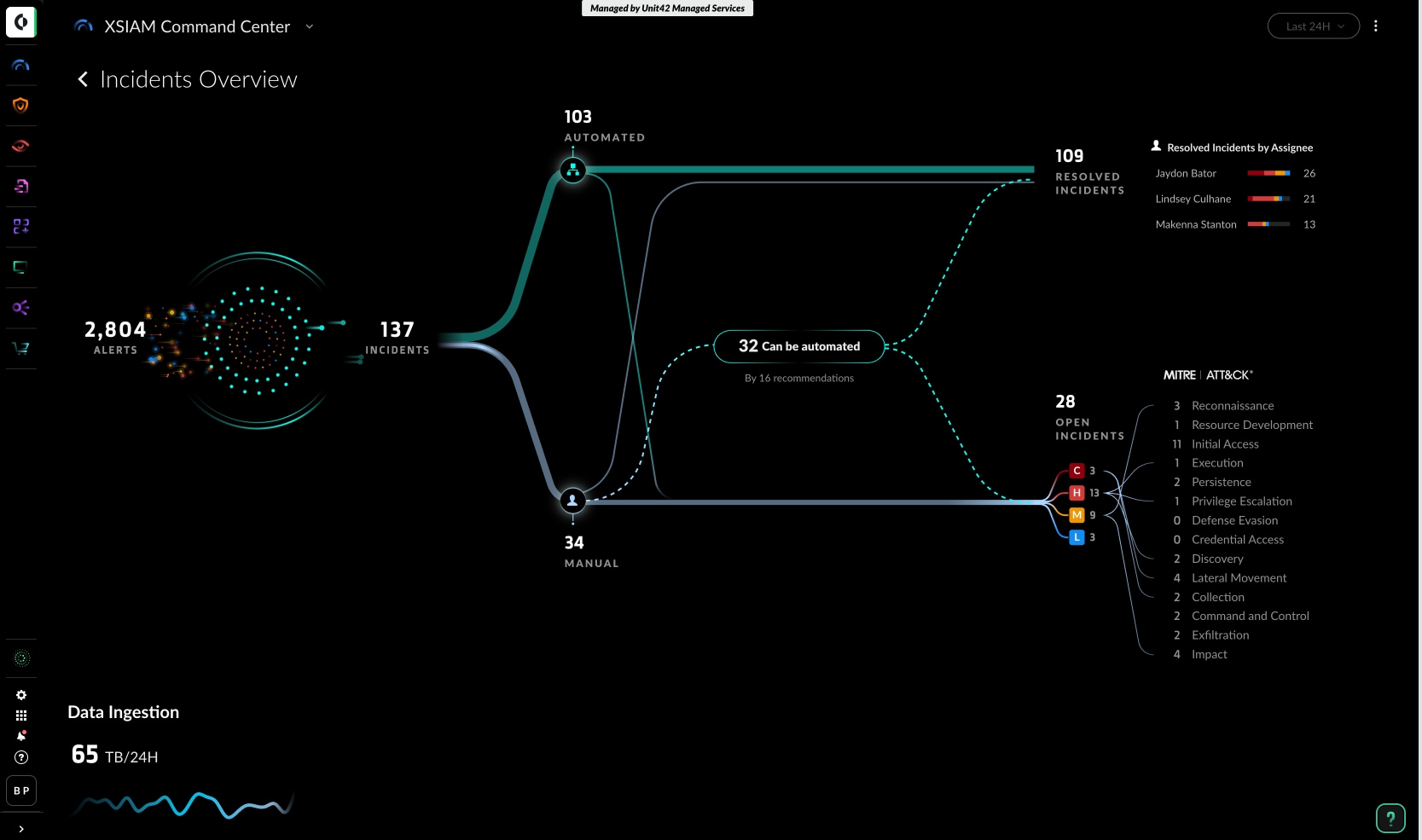
Speed ruled the trading floor: microsecond deals stitched together into billion-dollar days—yet security investigations still crawled. Splunk could see packets and queries, but every conclusion waited on a manual pivot. After acquiring a smaller firm, the parent company watched its new SOC slice through noise like a sharpened blade. Curiosity turned to action.
Endpoints, firewalls, cloud logs—all fed the same telemetry river. XSIAM stitched a living attack story in real time: the phishing email, the stolen token, the quiet lateral move into a forgotten server. One screen, nothing hidden. In the first quarter, 20 percent of daily logs moved off Splunk, and investigations that once sprawled across a dozen tabs opened inside a single panel. False positives dropped; the traders never felt a tremor.
The Regional Insurer
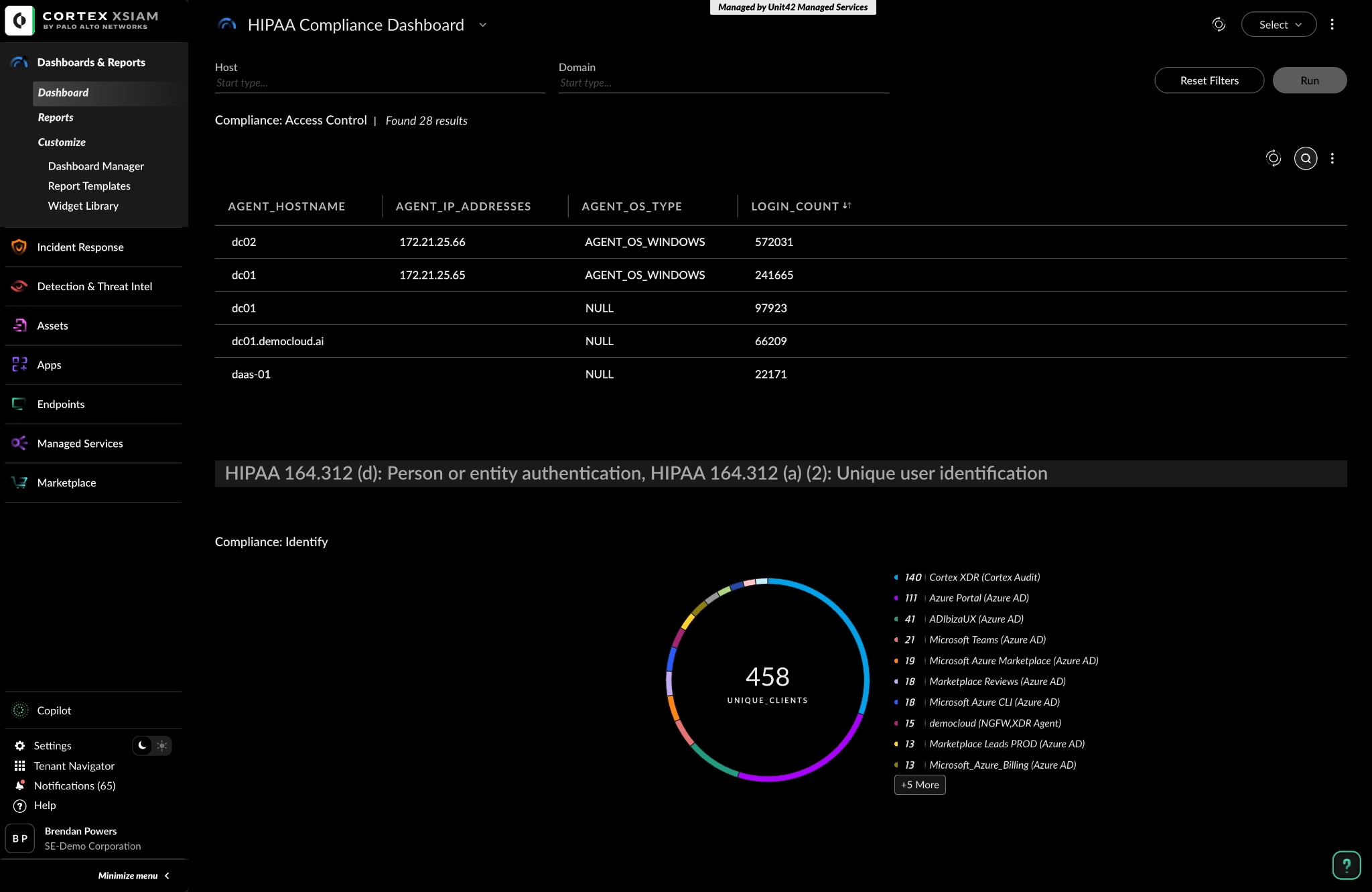
An insurer measures risk by the minute. Their legacy SIEM did not. Compliance scans crawled, correlation rules multiplied, ingestion costs ballooned. A third-party audit confirmed what the team already sensed: threat coverage was thin and response slow. They shifted SecOps to XSIAM while keeping observability data in Splunk.
Ingestion-based fees gave way to user-based tiers, and costs eased. MITRE-aligned detectors surfaced techniques the analysts had never caught. Playbooks fired off automatically—resetting passwords, blocking IPs, closing the loop before coffee cooled. 40 percent of logs drained from Splunk in the first month. The SOC’s ticket backlog halved, and the lead analyst took an uninterrupted vacation for the first time in years.
Where the Paths Converge
Different industries with a similar arc: Start with the logs that matter—authentication, endpoint, cloud—and let the platform learn. Watch as scattered alerts are consolidated into a single foundation, automation reinforces the structure, and a complete overhaul becomes a room-by-room renovation that never shuts down operations. Some teams retire Splunk entirely; others keep it for specialized workloads. Either way, the center of gravity shifts—from manual queries to live analytics, from console sprawl to a unified platform, from reaction to readiness with XSIAM.
If you’re weighing your own move, begin small, measure quickly, and watch the noise fade. When every second counts, modern SIEM ensures none are wasted. Explore the self-guided tour or book a live demo to see how your story could be read.