Every time you spin up a new virtual private cloud (VPC), you are likely paying twice for the privilege of securing it.
As enterprise CIOs accelerate digital transformation across AWS, Azure and Google Cloud, a hidden financial drain has emerged: the spiraling total cost of ownership (TCO) resulting from stitched-together architectures. While organizations rush to connect distributed workloads, many have inadvertently created brittle, expensive environments by layering third-party networking overlays on top of separate security appliances.
This shaky foundation is a strategic liability and an architecture problem. By consolidating these fragmented layers into the Palo Alto Networks multicloud security fabric (MSF), IT leaders can deliver immediate ROI, eliminate redundant licensing, and regain control over their budgets and risk posture immediately.
Eliminate the Double Tax on Your Infrastructure
Networking vendors charge you for connectivity, then force you to buy a separate firewall for actual protection. You currently face a double tax on your multicloud infrastructure when you rely on networking-first vendors that do not provide security.
The stitched architectures of network-only vendors force you into a no-win tradeoff. You can accept superficial, check-the-box security that is often reliant on generic open-source components that fail against modern AI-driven threats, or you can layer on a third-party security vendor to provide the actual protection you need.
The result is predictable: overlapping contracts, fragmented accountability for the same traffic, and duplicated licensing fees. This model inflates your TCO while leaving material gaps in AI governance, data protection and breach prevention, ultimately costing you more without adding strategic security that you really need.
So, why pay only for plumbing when you can invest in protection? A unified security fabric removes this financial inefficiency by converging networking and best-in-class security into a single platform. Enterprises reduce licensing bloat by replacing two disparate vendors with a single integrated solution.
You can easily imagine a CFO saying, "We are stopping the practice of buying overlapping tools. By moving to a single platform, we eliminate the connectivity tax and redirect that capital toward AI innovation."
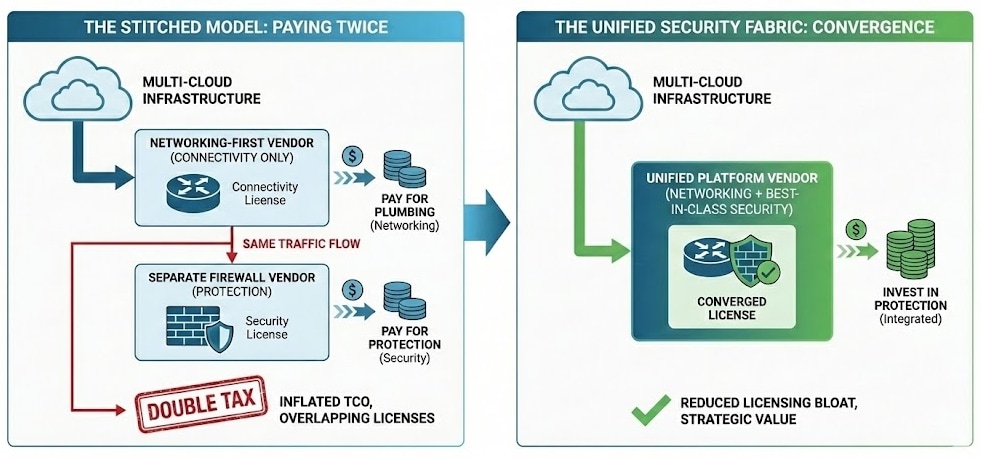
Separate networking and security creates a multicloud double tax.
Move from Layer 4 Blindness to Zero Trust for AI
Networking-centric tools may connect your clouds, but they often fail to secure them. Stitching together Layer 3 and Layer 4 routing with bolted-on security creates dangerous visibility gaps, particularly for east-west lateral movement where attackers often hide.
A networking-first approach cannot achieve Zero Trust because it lacks application-level visibility. The cost of a breach, which is measured in remediation expenses, regulatory fines and reputational damage, far exceeds the cost of proper prevention.
Shadow AI is the new risk. Your networking tools route traffic, but they don't know what that traffic is. Networking tools cannot see, for example, that sensitive customer data is being fed into an unapproved GenAI model. Only MSF provides the deep, Layer 7 inspection needed to instantly map your entire environment, including the elusive shadow IT and AI models, and block attack paths that stitched solutions miss.
Empower Developer Velocity; Don't Just Save Time
Manual workflows and complex integrations between separate networking and security layers can quickly put the brakes on your business agility. In a stitched architecture, the engineering hours required to configure traffic steering can delay critical application rollouts by weeks and significantly erode your competitive edge.
Instead, embed security into the pipeline. Automating the entire security lifecycle allows you to deploy protection in hours rather than weeks. With one-click orchestration, your teams can insert firewalls and configure policies instantly within their existing DevOps workflows, including Terraform and Ansible. This approach supports high-speed developer innovation without sacrificing control. What’s more, it allows you to focus your most expensive talent on high-value strategic initiatives instead of manual configuration tasks.
Achieve Continuous Compliance and Stop the Audit Nightmare
Fragmented visibility across multiple management consoles creates a hidden administrative burden that inflates your long-term operational costs. Proving compliance across three clouds with three different consoles takes weeks. When your teams must toggle between disparate dashboards for AWS, Azure and Google Cloud, the risk of human error skyrockets.
Simplification is strategic. Consolidating onto a single, security-first fabric simplifies your governance model. By managing your entire estate from Strata Cloud Manager, you ensure consistent posture across all workloads. This moves you from a chaotic, high-cost operation to a streamlined, predictable and secure enterprise environment that is designed to be audit-ready every single day.
Stop Funding Unnecessary Complexity
Don't let your cloud strategy become a financial anchor. Request a CLARA Assessment to see exactly how much the double tax is costing you and how much budget you can reclaim for innovation.