Unit 42 researchers at Palo Alto Networks recently analyzed crowdsourced data from security assessments of more than 200,000 infusion pumps on the networks of hospitals and other healthcare organizations using IoT Security for Healthcare from Palo Alto Networks. This topic is of critical concern for providers and patients because security lapses in these devices have the potential to put lives at risk or expose sensitive patient data.
The published findings show an alarming 75 percent of infusion pumps scanned had known security gaps that put them at heightened risk of being compromised by attackers. These shortcomings included exposure to one or more of some 40 known cybersecurity vulnerabilities, and/or alerts that they had one or more of some 70 other types of known security shortcomings for IoT devices.
Widespread Medical Device Vulnerabilities
There is already a vast array of information about known vulnerabilities and approaches for securing these devices, thanks to the efforts of medical equipment makers, security researchers, cybersecurity vendors and regulators who have spent the past decade working to better understand cyber risks associated with use of infusion pumps and other connected medical devices. For example, the U.S. Food and Drug Administration (FDA) announced seven recalls for infusion pumps or their components in 2021, and nine other recalls in 2020.
There are also initiatives led by industry and government aimed at standardizing device information and establishing baseline security criteria for manufacturing these devices. Yet the average infusion pump has a life of eight to 10 years. The widespread use of equipment whose functional life is much longer than the life of its operating system has hampered efforts to improve security.
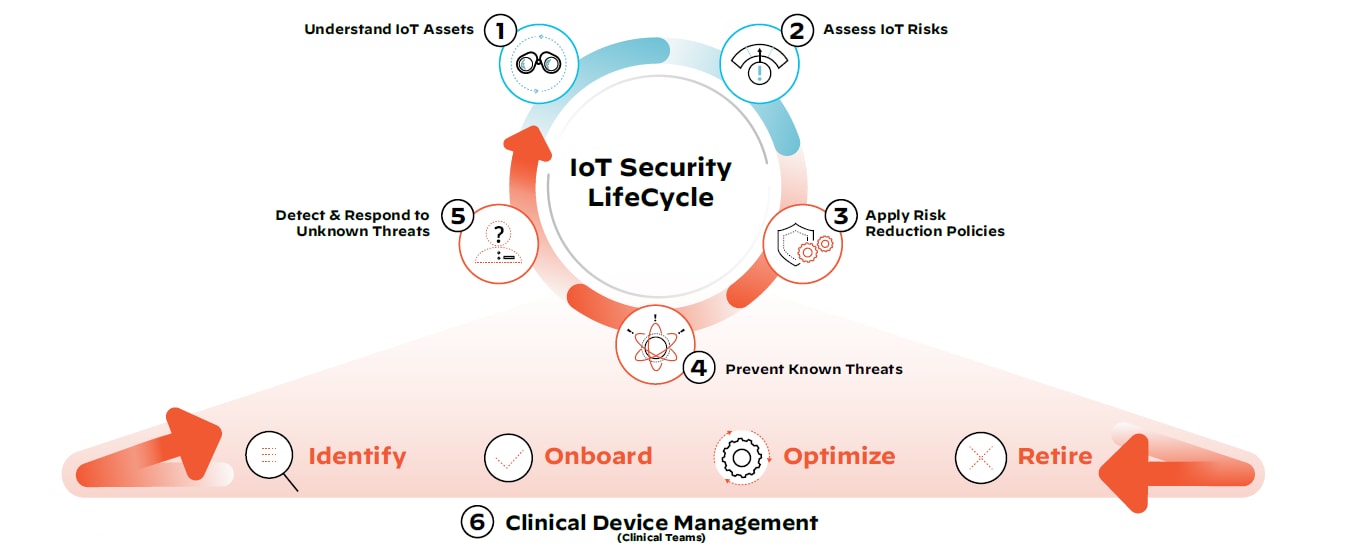
IoT and IoMT Security Lifecycle
What does this mean for healthcare organizations with vulnerable clinical and non-clinical devices on their network today? There are steps that can be taken immediately to reduce exposure to medical device threats. We call this the IoT Security Lifecycle approach:
Step 1: Discover all IoT devices, managed and unmanaged, clinical and non-clinical.
Employing device discovery will allow all stakeholders, including IT, security and biomedical teams, to get a full picture of what the medical device and IoT asset landscape looks like on the network.
Step 2: Assess the risk of all devices with continuous monitoring.
Accurate risk assessment allows IT security teams to continuously scrutinize devices, monitor their traffic patterns, segment devices and reduce the threat surface.
Step 3: Define and enforce policies to only allow trusted behavior.
Trust can be a vulnerability in and of itself. By implementing steps one and two, security teams have the visibility and context required to apply and enforce least privilege access policies.
Step 4: Prevent any known IoT attacks.
At this stage, a threat prevention mechanism that uses payload-based signatures to block advanced threats will ensure the most up-to-date security posture and defense against known threats across the network.
Step 5: Detect and respond to unknown IoT threats.
Crowdsourced data provides collective immunity by leveraging known medical device information, as well as behavioral analytics, to investigate previously unseen threats unique to the organization’s environment.
Step 6: Implement steps 1-5 in coordination with holistic clinical device management.
Operational device data can help clinical teams identify devices, securely onboard them for use as required, optimize their performance based on usage data and safely retire them in compliance with industry regulations.
Automation Is Key for Securing and Managing IoMT Devices
The discovery of security gaps in three out of four infusion pumps reviewed by Unit 42 highlights the need for the healthcare industry to redouble efforts to protect against known vulnerabilities, while diligently following best practices for infusion pumps and hospital networks.
Medical devices need to be understood in the context of a complete clinical device management methodology to minimize risk to patients and the network. The ideal methodology for healthcare operations relieves both network security and clinical teams from the day-to-day burdens of securing and managing these devices.
By assessing device risk and then applying positive, risk reduction policies that are prioritized and automated, organizations can begin reducing their attack surface. Only by automating this entire lifecycle – and continuously incorporating learnings to make further improvements – can the persistent vulnerabilities in connected medical devices be secured.
To learn more, read the Unit 42 research, Know Your Infusion Pump Device Vulnerabilities. And if you’re attending HIMSS this week, schedule a time to speak with our healthcare cybersecurity experts or visit us in booth #1059.