Last week I had a moment of clarity while studying the HackerOne leaderboard. An AI agent named XBOW claimed the top spot and now sits at number twelve. I reviewed its attack traces. I saw it chain together a sophisticated padding oracle attack on a custom crypto CAPTCHA. I also watched it dissect a GraphQL API and uncover a critical insecure direct object reference flaw. (It's worth noting that our own Unit 42 team recently published an article detailing the use of LLMs for detecting broken object level authorization (BOLA) attacks).
Exploits at this level go beyond mere scanner findings. They demonstrate genuine, machine-speed logic targeting complex business processes.
My realization mirrors wider industry anxiety. A recent Palo Alto Networks study found that 61% of organizations fear AI-powered attacks will compromise sensitive data. They’re right to be concerned. With nearly one in five cyberattacks, data exfiltration now happens within the first hour of compromise. Unit 42 testing shows AI assistance cuts time to exfiltration from days to just 25 minutes. Meanwhile security teams still require an average of 145 hours to resolve a single alert. Our defensive timeline remains hopelessly mismatched with offensive reality.
Defenders once counted on grace periods. Those days have ended.
Cybersecurity’s Machine-Gun Moment
We’re living in cybersecurity’s machine-gun moment. We run a defensive playbook of methodical, human-driven operations while adversaries unleash automated, overwhelming attacks.
Relying on a "scan-and-patch" cycle is like planning a week-long fortification project in the middle of an ambush.
Our industry has poured immense resources into building an impenetrable fortress. We shifted left, armed developers with static application security testing (SAST) tools and hunted for every flaw. The secure by design philosophy, for all its good intentions, is predicated on achieving a state of near-perfect invulnerability. The pursuit of perfection, of course, becomes a fool’s errand when an adversary can find and exploit an unknown flaw in the time it takes you to read this sentence. The wall will fail. The defining question is what will happen in the five minutes after that.
The Pivot to Engineering for Resilience
Since we can’t guarantee perfect prevention, we need to shift our strategy from chasing invulnerability to engineering for security synergy. The new mandate is resilience by design.
Visualize this approach using the swiss cheese model. Every defensive layer in our security stack, including code scanning, IAM policies, network segmentation and runtime protection, is a slice of cheese with unavoidable holes. An attacker succeeds only when holes in every layer align to create a direct path.
A resilient architecture based on the Swiss cheese model relies on multiple, diverse defense layers. A vulnerability missed by a static application security testing scanner becomes useless under a least-privilege IAM role. A misconfigured IAM role receives neutralization from a runtime agent that detects and blocks anomalous behavior. Layer synergy prevents hole alignment.
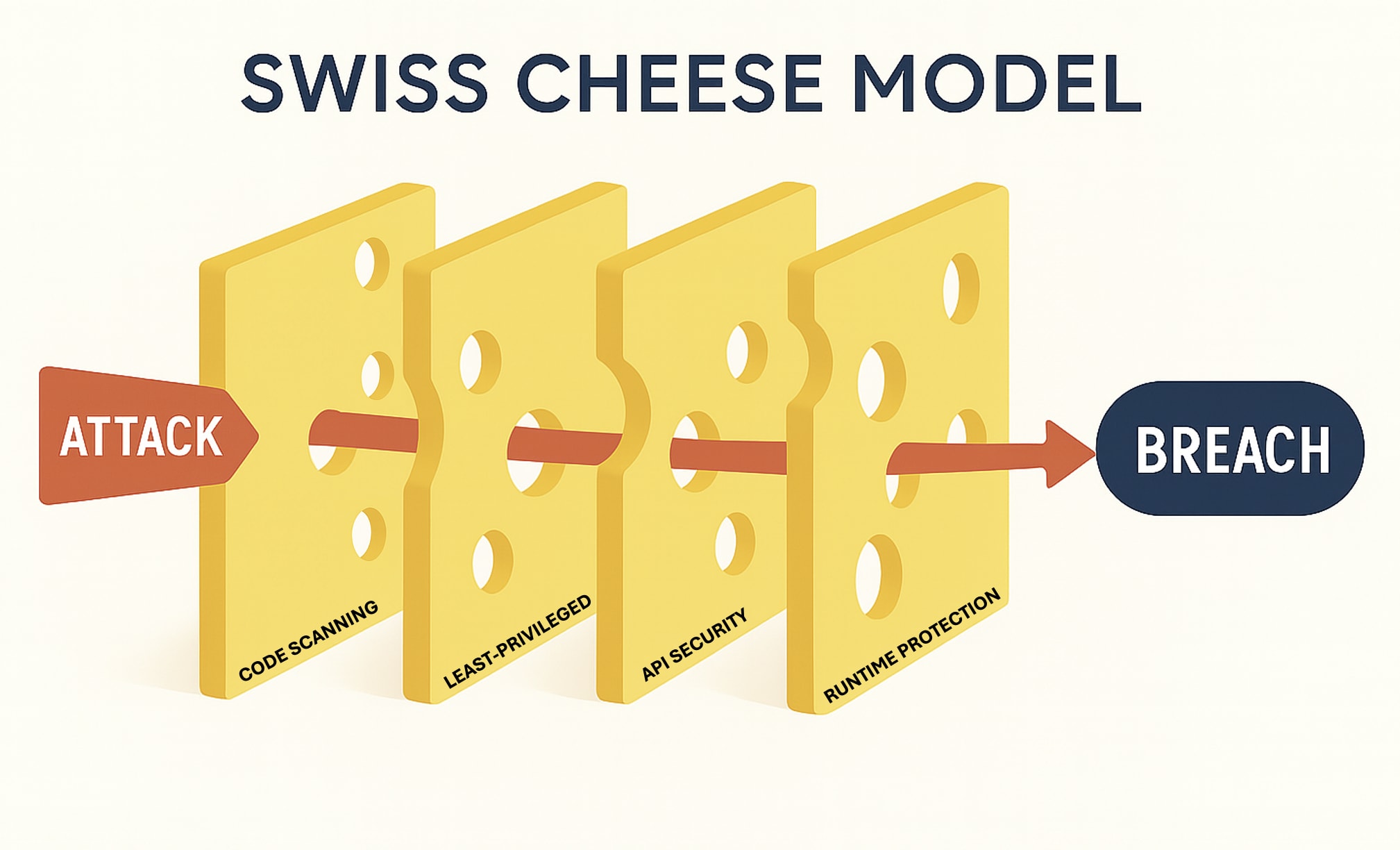
A resilient architecture built according to this principle requires a fundamental change in how we build software and measure security success. It stands on four critical concepts.
Aggressive Containment
Modern cloud-native systems must be architected as a series of segmented, isolated compartments to prevent a breach in one microservice or container from cascading.
The most effective way to achieve isolation is by assigning each workload a strictly scoped, least-privileged IAM role. A compromised container then becomes a dead end for the attacker. Imagine a service whose IAM role grants only read access to a single S3 bucket. A breach of that service remains instantly contained. The attacker can’t access other databases, spin up new VMs or retrieve secrets. Lateral movement stops before it starts. I demonstrated this principle years ago in a Dark Reading article, detailing how a compromised Lambda function becomes neutralized by a minimal IAM role.
Real-Time Visibility
Runtime security agents deployed directly on workloads provide the intelligence required for resilience. They detect attacks in real time.
Organizations relying solely on agentless scanning measure mean-time-to-detect in days. Those deploying a runtime agent directly on workloads achieve continuous detection within minutes.
A resilient system depends on a single source of truth. It must correlate application vulnerabilities with runtime exploit attempts and cloud misconfigurations with lateral movement. Unified telemetry enables the split-second decisions resilience demands.
Consider a typical cloud breach. An attacker exploits a container vulnerability, escalates privileges using leaked IAM credentials and moves laterally. A unified platform sees the entire attack path unfold in real time.
Immediate Response
Detection alone holds no value if response lags behind an attack. Manual investigation workflows collapse under machine-speed attacks. Resilient applications must use real-time defenses. When runtime agents detect the exploitation of a known vulnerability, the system must instantly map the attack path and execute containment. The precision required for automated containment, where a false positive could disrupt business, demands the highest degree of detection accuracy.
We need to remove the bottleneck. Imagine an API protected by a runtime agent. Having detected an exploit, the agent alerts the security platform, which instantly severs the malicious connection, freezes the compromised process for forensic analysis and quarantines the container from the network — all before a human analyst is even aware of the event.
Guarantee Operational Survival
An automated response is powerful, but only if the cure isn't worse than the disease. The final pillar of resilience ensures the business survives its own defenses.
A resilient system must ensure core business functions persist even when defenses isolate components. A financial trading platform, for example, should continue processing transactions if an auxiliary market data analysis service becomes quarantined.
Designing for graceful degradation goes beyond high availability. It ensures business continuity in a hostile digital environment and validates the resilience strategy’s ultimate goal — operational survival.
Resilience by Design: Beyond the First 5 Minutes
To answer the defining question — what happens in the five minutes after breach? — we must redefine success. Security no longer means preventing every compromise. It means ensuring that even at machine speed, attackers can’t achieve their objectives.
Resilience by design represents an evolution in strategic thinking. Organizations adopting this mindset will set the new standard in cybersecurity, prevailing not by the perfection of defenses, but by their power to endure.
To learn more about a unified approach to security, read Breaking Barriers in Enterprise Security: An Executive Guide to Cloud Security and SOC Convergence.